Threat of Session Hijacking and Steps to Prevent Them
Authors: Abhinand Gokhala K., Harikrishna Kelappurath
Sometimes when you try to open your Facebook profile it opens without asking username or password. It might have been because you logged in previously and forgot to log out. Did you ever try to understand why this is happening and it's significance?
It is because something is stored in your browser and is sent to the server when you accessed it again. So something which is highly confidential is stored in your web browser. What will happen if someone stole those details?
If someone gets that detail he could access the profile, this is called session hijacking.
This can be better explained using the scenario of the hospital system, i.e patient as the client, the hospital, doctor and the whole medical system can be considered as the server. First time when the patient takes an appointment, a token will be given to him and the case record with that token id will be retained in the hospital itself. Now whenever the patient visits a doctor, the doctor will get the previous health details of the patient with that token id from the hospital records. Hospital systems identify each patient using their token id. So anyone can get the treatment details of the patient using the token id of that patient. This is a real-life session hijacking situation. And we can also say that here token id, hospital system, and patient are referred to as session-id, server, and client respectively.
In this article we are going to explain what is session hijacking and how it is possible. Before that let’s look at some of the key terms used here.
What is Meant by a Client?
People sometimes mistakenly assume that the client referred to here is the person who sits in front of a computer system. But for a server, a web browser in a system is one client. For instance, consider two computer systems A and B. Firefox in A and Firefox in B are different clients. Firefox in A and Chrome in A are also different clients.
What is Session Information and Session ID?
The necessary information about a particular client stored on the server side is called Session Information. Session information is secure inside the server. From the server side, we can create session information with a unique id, this unique id is called session id. After creating a session, the session id is sent to the corresponding client. The client stores the session id as a session cookie. All further communication between the client and server includes sending the session cookie value from client to server.
For example, if you log in to a web application the following process will happen.
- Client sends a request to login to the application with username and password.
- Server creates a unique id (Session id) then creates a file with that session id as file name.
- Server saves necessary data about the client in the created file, for example: User id of logged user.
- Server sends that unique id to the client for storing that unique id as cookie.
- If the client accesses the profile page of that application, the web browser sends the stored cookies with that request.
- Server checks whether the session file corresponding to the session cookie value is present in the server. If session file is present, the server reads information in that file. From that the server will get the logged user id. Then server sends requested information related to that user id to the logged user.
- Similar to the above process, for all requests, the client will pass session cookie value to the server.
For a general understanding
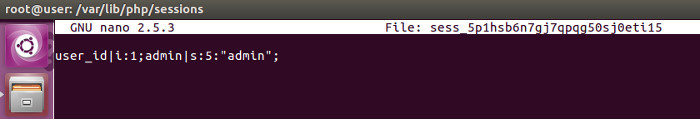
This is a session file created on the server. PHP session files are stored in ‘/var/lib/php/sessions’ in default. Here filename is the session id which are random characters followed by ‘sess_’. In the session, the data is stored in the following format ‘data name|type: length: value’. In the above picture two data are stored, user_id and admin. In the case of user_id, the type is i(i denotes it is an integer value and s denotes string), length of the value is 1. And value of user_id is 1.
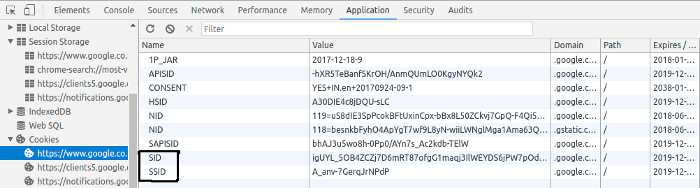
This picture shows the cookies stored in one such web browser. In the developer tool option, you can see the different types of cookies stored in the browser.
What is Session Hijacking?
Session hijacking is mimicking a different person by using that person’s session id. That is, if person A gets the session cookie information of person B and A stores that cookie in his web browser manually (similar to how B has stored the cookie in his browser). Then A can get the same access of B if that session file is present in the server. This is called session hijacking.
How is Session Hijacking important?
Consider that a hacker gets the session cookie value of the bank application of a person, the hacker can get full access to that person‘s profile from the bank application. It is a big threat.
There are various ways in which session hijacking can be prevented. The preventive measures from the server side include cookie’s validation, cookie regeneration, session timeouts. Despite all these, there are limitations to what can be done from the server side. Complete prevention can be ensured only from the client side by making sure that the cookie value is kept safe through anti-malware software and by always logging out after usage.
XSS is one of the main methods used by hackers to steal cookie value from other clients.
To prevent XSS type of attack, developers can use HTML entities in the front end view of websites. This makes the data entered by users to always pass through functions to convert to HTML entities before it is shown in the front end view. In this way we can avoid XSS attack.
We will cover XSS in detail in another article. Are you concerned about the security aspects of your website development? We can help you!