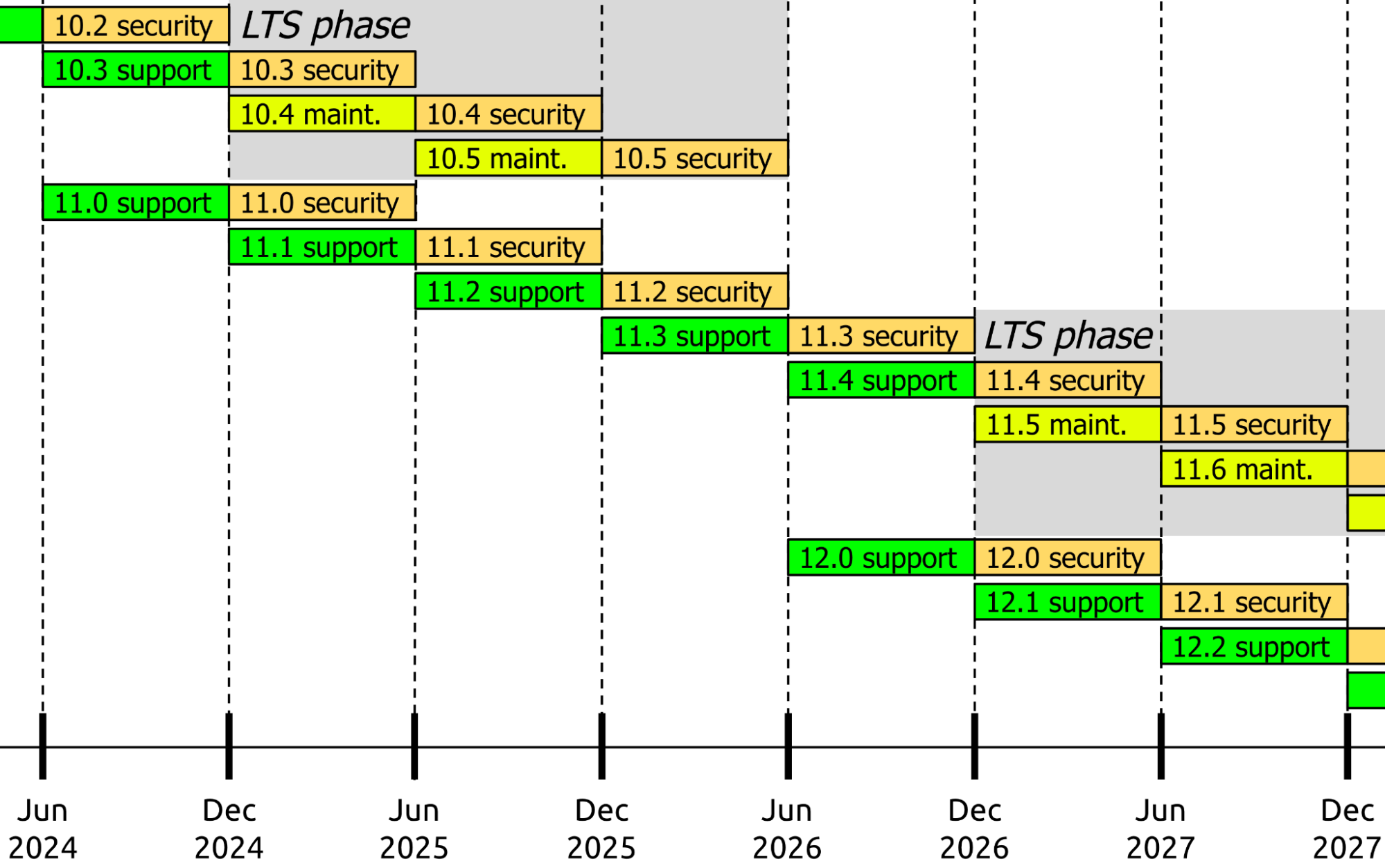
The digital landscape demands agility and foresight. With Drupal's revised release and support plan, users now have a reliable framework to stay ahead of the curve. Unpredictable release schedules often created uncertainty and complexity in maintaining Drupal-powered websites. However, those days are now behind us. Drupal has introduced a significant shift in its release and support strategy, empowering its users to confidently plan for the future and address challenges with newfound clarity. Let's explore what this means for the Drupal community